Trustico® Online Security Blog
Say informed with the latest SSL Certificate news, security updates, and industry insights. Our articles cover everything from SSL Certificate management best practices to emerging cybersecurity trends and industry news.

Business E-Mail Compromise (BEC) Attack
BEC attacks involve cyber-criminals impersonating legitimate business e-mail accounts to defraud companies and their employees. These sophisticated attacks often target organizations that conduct wire transfers or work with foreign suppliers.
Business E-Mail Compromise (BEC) Attack
BEC attacks involve cyber-criminals impersonating legitimate business e-mail accounts to defraud companies and their employees. These sophisticated attacks often target organizations that conduct wire transfers or work with foreign suppliers.
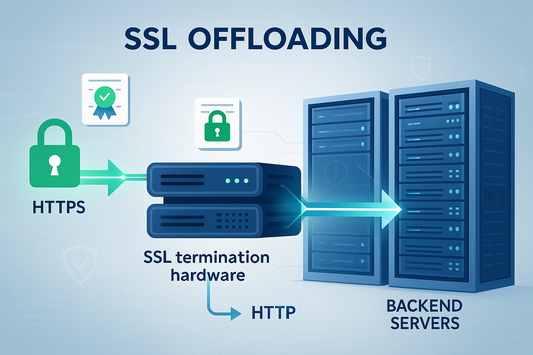
SSL Offloading - Types, Benefits, and Best Prac...
SSL Certificate offloading refers to the process of removing SSL Certificate encryption processing from web servers by handling it at the load balancer level.
SSL Offloading - Types, Benefits, and Best Prac...
SSL Certificate offloading refers to the process of removing SSL Certificate encryption processing from web servers by handling it at the load balancer level.
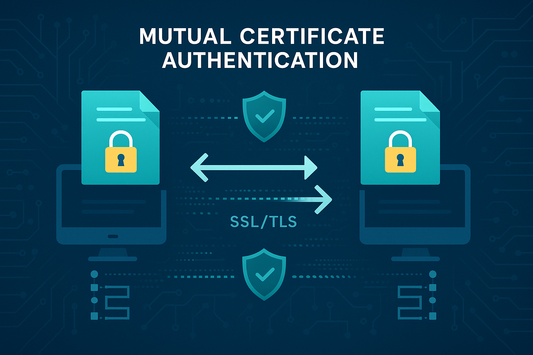
Mutual Certificate Authentication - Two-Way SSL...
As a leading provider of both Trustico® and Sectigo® branded SSL Certificates, we offer comprehensive solutions for organizations requiring secure, bidirectional authentication between clients and servers.
Mutual Certificate Authentication - Two-Way SSL...
As a leading provider of both Trustico® and Sectigo® branded SSL Certificates, we offer comprehensive solutions for organizations requiring secure, bidirectional authentication between clients and servers.
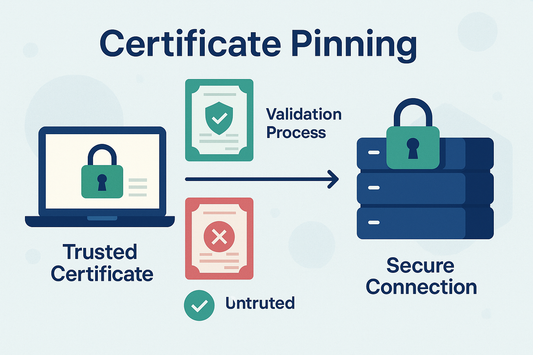
Certificate Pinning - How it Works
SSL Certificate pinning is a crucial security measure that enhances the protection provided by Trustico® SSL Certificates. SSL Certificate pinning is a security technique that associates a specific SSL Certificate...
Certificate Pinning - How it Works
SSL Certificate pinning is a crucial security measure that enhances the protection provided by Trustico® SSL Certificates. SSL Certificate pinning is a security technique that associates a specific SSL Certificate...
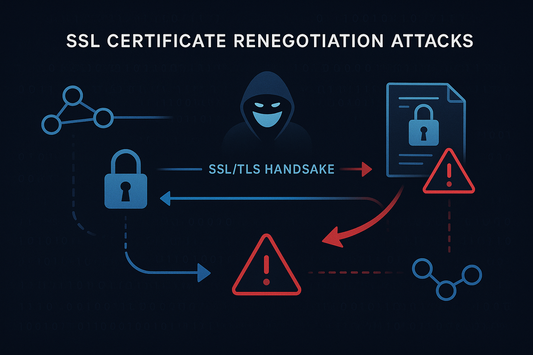
SSL Certificate Renegotiation Attacks
An SSL Certificate renegotiation attack occurs when a malicious actor exploits the SSL Certificate / TLS handshake process to inject malicious data into an encrypted session.
SSL Certificate Renegotiation Attacks
An SSL Certificate renegotiation attack occurs when a malicious actor exploits the SSL Certificate / TLS handshake process to inject malicious data into an encrypted session.

SSL Termination - How Does It Work
SSL Certificate termination refers to the process where encrypted SSL Certificate / TLS traffic is decrypted at a load balancer before being sent to web servers.
SSL Termination - How Does It Work
SSL Certificate termination refers to the process where encrypted SSL Certificate / TLS traffic is decrypted at a load balancer before being sent to web servers.

Free SSL Certificates vs Premium
While free SSL Certificate options have emerged in recent years, businesses concerned with comprehensive security, brand reputation, and customer trust continue to choose premium SSL Certificates from established providers like...
Free SSL Certificates vs Premium
While free SSL Certificate options have emerged in recent years, businesses concerned with comprehensive security, brand reputation, and customer trust continue to choose premium SSL Certificates from established providers like...

Distinguished Name (DN) Information
When applying for an SSL Certificate through Trustico® the Distinguished Name forms part of the Certificate Signing Request (CSR) and plays a vital role in establishing the identity and authenticity...
Distinguished Name (DN) Information
When applying for an SSL Certificate through Trustico® the Distinguished Name forms part of the Certificate Signing Request (CSR) and plays a vital role in establishing the identity and authenticity...
Stay Updated - Our RSS Feed
There's never a reason to miss a post! Subscribe to our Atom/RSS feed and get instant notifications when we publish new articles about SSL Certificates, security updates, and news. Use your favorite RSS reader or news aggregator.



